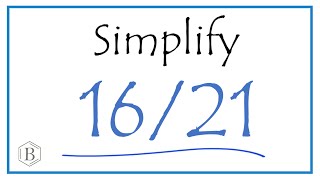In this video, we cover the theory behind Access Control vulnerabilities, how to find these types of vulnerabilities from both a white box and black box perspective, how to exploit them and how to prevent them.
▬ ✨ Support Me ✨ ▬▬▬▬▬▬▬▬▬▬
Buy my course: [ Ссылка ]
▬ 📖 Contents of this video 📖 ▬▬▬▬▬▬▬▬▬▬
00:00 - Introduction
00:28 - Web Security Academy Course ([ Ссылка ])
01:39 - Agenda
02:25 – What is Broken Access Control?
22:50 – How to Find Access Control Vulnerabilities?
30:29 – How to Exploit Access Control Vulnerabilities?
34:40 – How to Prevent Access Control Vulnerabilities?
39:00 – Resources
39:15 - Thank You
▬ 🔗 Links 🔗 ▬▬▬▬▬▬▬▬▬▬
Video slides: [ Ссылка ]
Web Security Academy OS Command Injection: [ Ссылка ]
Cross-Origin Resource Sharing Playlist: [ Ссылка ]
Rana's Twitter account: [ Ссылка ]
Hacker Icons made by Freepik: [ Ссылка ]
Broken Access Control | Complete Guide
Теги
securityweb securityowaspopen web application security projectCross-Origin Resource Sharing (CORS) | Complete Guideportswiggerweb security academypythonoffensive securitybug bountyscriptingburpburp suiteosweoffensive security web expertbroken access controlbacaccess controlaccess control vulnerabilititesowasp top 10owasp top 10 2021










![Фонарик станет вечным! Добавь в него эту схему не пожалеешь! [Компанец Д А]](https://i.ytimg.com/vi/nrpo0ic_fds/mqdefault.jpg)