[ Ссылка ]
Configured OSPF routing protocol on the routers
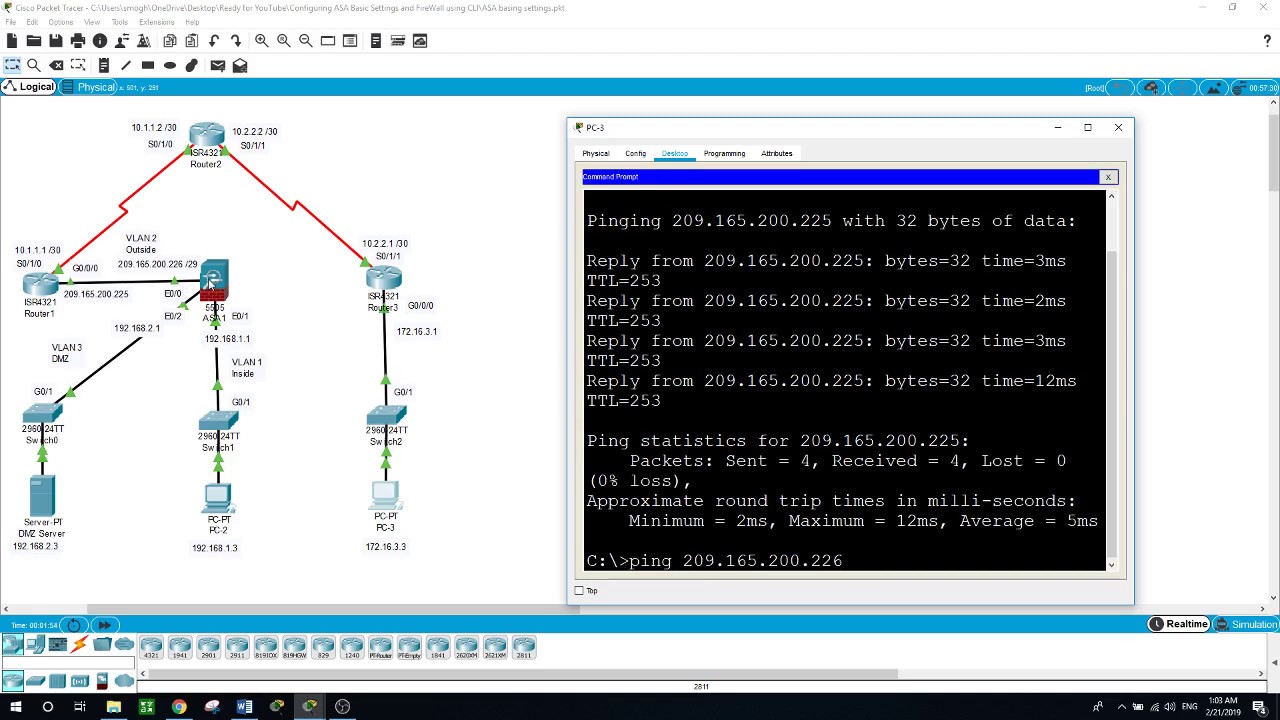
Now you can ping from PC-3 the interface of 209.165.200.225 of Router1.
# ping 209.165.200.225
• Use the show version to determine the aspects of this ASA device.
# show version
# show file system
# show flash
# show disk0
# hostname ASA
# domain-name ccnasecurity.com
• Configure the enable password as cisco
# enable password cisco
• For VLAN 1 interface (inside) IP address 192.168.1.0 /24, the security level of 100
# interface vlan 1
# nameif inside
# ip address 192.168.1.1 255.255.255.0
# security-level 100
# interface vlan 2
# nameif outside
# ip address 209.165.200.226 255.255.255.248
# security-level 0
• Use the following commands to display the status of the ASA interfaces
# show interface ip brief
# show ip address
# show switch vlan ,.
# ping 192.168.1.1
.# ping 209.165.200.226 should fail.
# route outside 0.0.0.0 0.0.0.0 209.165.200.225
# show route
• Verify that the ASA can ping Router1 S0/1/0 IP address 10.1.1.1
# ping 10.1.1.1
Create a network object inside-net and assign attributes using subnet and nat commands
# object network inside-net
# subnet 192.168.1.0 255.255.255.0
# nat (inside,outside) dynamic insterface
# end.
# show run
# ping 209.165.200.225
Then run this command:
# show nat
We will create the class-map, policy-map and then service policy, and add the inspection of ICMP traffic to the policy map
- Create the class map ( name is CLASS)
# class-map CLASS
# match default-inspection-traffic
# exit
- Next the policy map ( name is POLICY)
# policy-map POLICY
# class CLASS
# inspect icmp
# exit
# service-policy POLICY global
# dhcpd address 192.168.5-192.168.1.36 inside
Now, enable the DHCP within the ASA to listen to DHCP client requests on the enable interface (inside)
# dhcpd enable inside.
- We will create a user named admin with a password of admin
# username admin password admin
- Now, we will configure AAA to use the local ASA database for SSH user authentication
# aaa authentication ssh console local
# crypto key generate rsa modulus 1024
# no ( when prompted).
# ssh 192.168.1.0 255.255.255.0 inside
# ssh 172.16.3.3 255.255.255.255 outside ( just one host).
# ssh -l admin 209.165.200.226
# ssh – admin 192.168.1.1
• # interface vlan 3
• # ip address 192.168.2.1 255.255.255.0
# no forward interface vlan 1
# nameif dmz
# security-level 70
- Let us now assign ASA physical interface E0/2 to DMZ VLAN 3 and enable the interface
# interface ethernet0/2
# switchport access vlan 3
- Let us run few commands to verify what we did so far
# show interface ip brief
# show ip address
# show switch vlan
• Let us now configure static NAT to the DMZ server.
# object network dmz-server
# host 192.168.2.3
# nat (dmz,outside) static 209.165.200.227
• Now let us configure an ACL
• # access-list DMZ-OUT permit icmp any host 192.168.2.3
# access-list DMZ-OUT permit tcp any host 192.168.2.3 eq 80
# access-group DMZ-OUT in interface outside.































































![[Урок Revit] Плинтусы и другие линейные объекты с профилем Часть 1](https://i.ytimg.com/vi/NBY8O5Mhwqk/mqdefault.jpg)






